Blogs
- All
- Governance
- Risk
- Compliance
- General Cyber Security
Defense Cyber Security has been certified by Saudi Aramco as an authorized audit firm to conduct the assessments and issue the CCC against the SACS-002 Third Party Cybersecurity Standard
Defense Cyber Security has been certified by Saudi Aramco as an authorized audit firm to conduct the assessments and issue the Cybersecurity Compliance Certificates (CCC) against the SACS-002 Third Party Cybersecurity Standard. This makes Defense Cyber Security one of only eleven audit firms in Saudi Arabia authorized to conduct these assessments. Saudi Aramco launched its […]
Types of phishing attacks
In our previous article, we explained the general idea behind phishing. We also stated that there are different types of phishing attacks which we all need to know about in order to identify and protect ourselves from them. Over the years, some of these computer phishing attacks have become more sophisticated, making it more difficult to recognize them; It is […]
How to recognize and avoid phishing scams
Phishing is one of the most used attacks by cyber criminals who want to gain personal data, banking credentials, and user accounts. Phishing is not a new threat, in fact it has been used for a long time, however, victims of this type of attack are still on the rise. In this article we are going to explain […]
فيروسات الفدية: ما هي وما مخاطرها وكيف تحمي نفسك منها
في يونيو 2017، انتشر فيروس الفدية “نيتيا” كالنار في الهشيم عبر شبكة الانترنت في أوكرانيا. استخدم هذا الفيروس ثغرة في تحديث لبرنامج محاسبة أوكراني مشهور ليلتهم المعلومات في ملايين الأجهزة واضعاً ما يقارب 2000 شركة أوكرانية تحت رحمته بينها فروع لشركات عالمية كشركة النقل البحري المعروفة ميرسك. في هذا المقال، سنحاول أن نشرح باختصار وموضوعية النقاط الأساسية الخاصة بفيروسات […]
Secure password protocols
Your organization can take every precaution to prevent a cyber-attack – firewalls, antivirus, antimalware, spam filter, etc. - but their greatest vulnerability is not lurking in the cyber shadows, they are sitting in your office. The failure to adhere to the employee password policy requirements could put your whole business at risk. How to Enforce Password Policies for Your Business Putting a password policy in place for […]
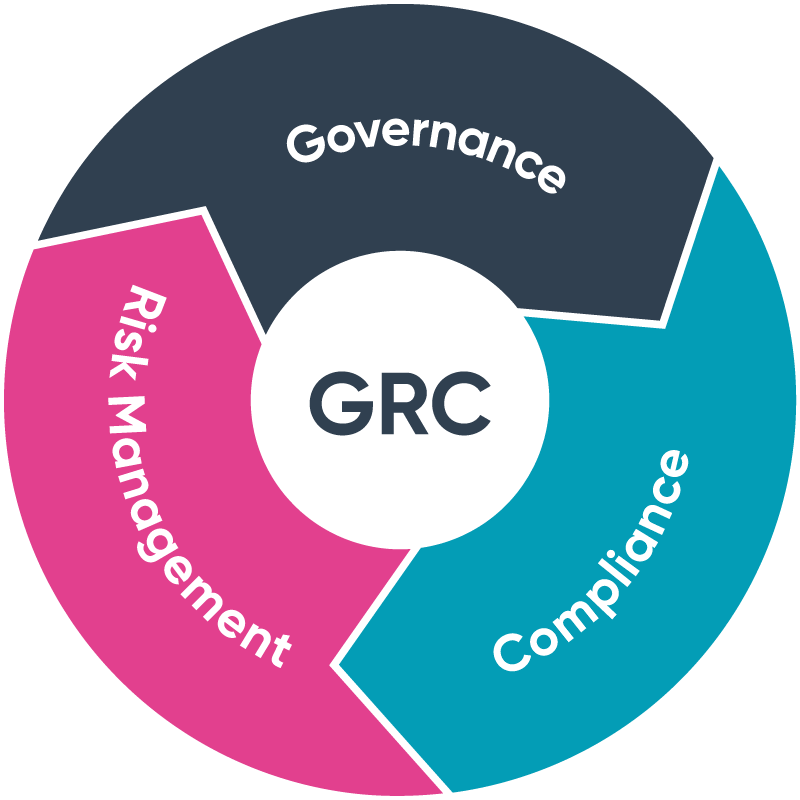
What is a Governance, Risk and Compliance (GRC) culture?
Before adopting new technologies, companies must train their teams and stabilize its corporate governance, the risk management and compliance. This must become a culture for all areas of the company. It would not make sense to reinforce corporate governance, risk management and regulatory compliance just to comply with legal requirements if there is no organizational culture that aligns these three aspects […]